Cybersecurity is a major issue for the Department of Defense and federal contractors. In an effort to streamline the certification process and ensure that cybersecurity measures are being implemented correctly, the U.S. Department of Defense has created a model called Cybersecurity Maturity Model Certification (CMMC).
The model provides a structured approach for assessing whether or not your business is properly managing risk in your IT infrastructure by requiring you to pass an independent third-party assessment first before bidding on any DOD contracts involving handling sensitive information or unclassified export control data such as ITAR-controlled technical data sets (ITDS).
A Unified Standard
The Cybersecurity Maturity Model Certification (CMMC) is a unified standard used across the Department of Defense to ensure that cybersecurity measures are being implemented correctly by federal contractors. The CMMC certification process includes assessments and certifications for compliance with industry best practices, which helps protect against cyber threats, improves the security of networks and data, and prevents unauthorized access.
The CMMC program is based on five key cybersecurity maturity pillars: risk management; information security; incident response; configuration management; and operational control. These pillars are designed to provide an overall assessment of how well a contractor’s cyber program is performing in each area based on their current level of maturity.
CMMC 2.0 vs CMMC 1.0
CMMC 2.0 will be more streamlined, easier to implement and use, and easier for your teams to understand.
In September 2020, the DoD published an interim rule to the DFARS in the Federal Register (DFARS Case 2019-D041), which implemented the DoD’s initial vision for the CMMC program (“CMMC 1.0”) and outlined the basic features of the framework (tiered model, required assessments, and implementation through contracts). The interim rule became effective on November 30, 2020, establishing a five-year phase-in period.
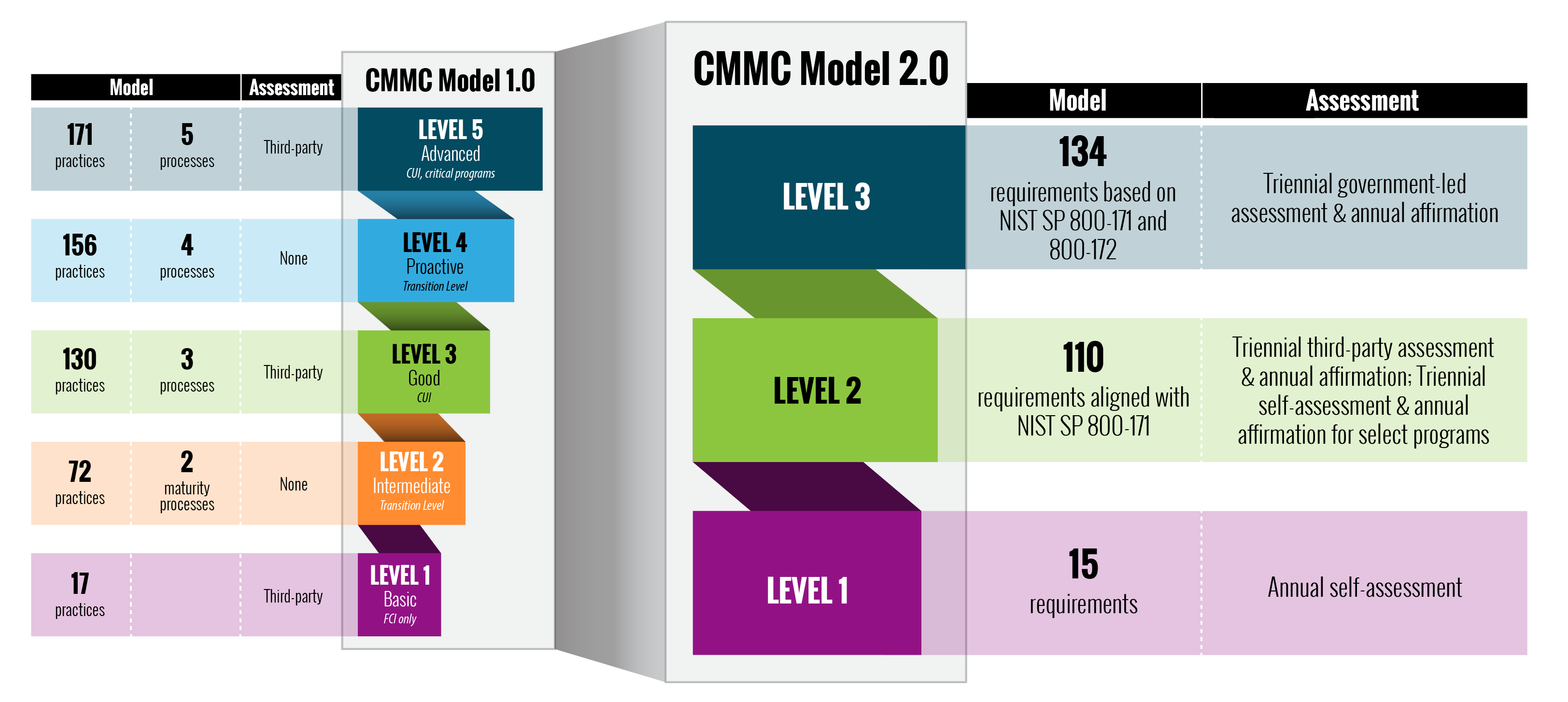
Photo from the Acquisition & Sustainment website.
With the implementation of CMMC 2.0, the Department is introducing several key changes that build on and refine the original program requirements. These are:
Streamlined Model
The model was updated from 5 to 3 compliance levels to only focus on the most essential requirements. This model also aligns with the National Institute of Standards and Technology (NIST) cybersecurity standards.
Reliable Assessments
Lowers the cost by allowing all companies at Level 1 (Foundational), and a subset of companies at Level 2 (Advanced) to demonstrate compliance through self-assessments. The model also increases oversight of professional and ethical standards of third-party assessors.
Flexible Implementation
The new model also allows companies, under certain limited circumstances, to make Plans of Action & Milestones (POA&Ms) to achieve certification. It also allows waivers to CMMC requirements under certain limited circumstances.
Third-Party Assessors
The new CMMC assessments will be administered by an independent third party that has gone through the CMMC-AB accreditation process. These entities are called CMMC Third Party Assessment Organizations (C3PAOs) and the CMMC Assessors and Instructors Certification Organization (CAICO).
Accredited C3PAOs will be listed on the CMMC-AB Marketplace.
The accreditation process for these third-party assessors involves multiple steps over several months, including a review of each company's staff qualifications and experience, compliance with industry standards and quality assurance procedures, as well as security measures for data storage and protection against tampering or unauthorized access to test results.
Contractors Working with Sensitive Material Must Comply
CMMC 2.0 is a unified standard used across the Department of Defense to ensure that cybersecurity measures are being implemented correctly by federal contractors.
In order for you to bid on Department of Defense contracts that involve handling sensitive information or unclassified export control data such as ITAR-controlled technical data sets (ITDS), your company must comply with CMMC standards. The purpose of this blog is to summarize what those standards are so that you can understand how they work for you—and why it's important for all your employees who handle sensitive information at work every day.
To Close Out
As we can see, the Cybersecurity Maturity Model Certification (CMMC) will be the standard used across the Department of Defense to ensure that cybersecurity measures are being implemented correctly by federal contractors.
All the experts are saying don’t wait to comply with these standards. You can really set yourself apart as a federal contractor if you comply with these standards early and, if you are able, get assessed early. Doing so will make you one of the few with the certifications.
If you need any help understanding CMMC 2.0 further or if you need help getting the process started, feel free to reach out to us at US Federal Contractor Registration (USFCR).
We have compliantly assisted more than 300,000 contractors with the System for Award Management (SAM) along with a multitude of government agencies registrations. Trust in USFCR to be your partner for success. Learn more about CMMC compliance.
To speak with a Registration and Contracting Specialist about CMMC Compliance, Call:
RELATED ARTICLES
Federal Contract Compliance for DoD Contractors
Cybersecurity Compliance for Non-DoD Federal Contract
NSF Investing $69 Million Annually in Cybersecurity




